Ahmad Hakimi
Sales Engineer Hybrid | SaaS & AI Solutions | Turning Technical Depth Into Revenue
I design, demo, and sell solutions that turn complex tech into clear business wins.
About My Journey
I’ve spent the last decade living at the intersection of tech and business. From enterprise IT at Amazon, Colliers, and USPS… to building SaaS tools like FlippAI and generating $300k+ through The Flipping Ninja… I’ve always been obsessed with one thing: turning technical systems into real business wins.
Now I’m pivoting into Sales Engineering—where I get to do exactly that every day: run discovery, demo solutions, handle objections, and show clients the real value behind the tech.
Featured Projects
Here’s some of the stuff I’ve built over the years——apps, tools, experiments, and even a few scrappy side hustles. Every project sharpened my ability to spot problems, design solutions, demo them in plain English, and get people to say ‘yes.’
FlippAI is an AI-powered SaaS app that automated ad creation and tracked 3,000+ item flips. I built the entire stack (Airtable APIs + GPT integration), then demoed it live to users, handled objections, and closed paying subscribers. The platform generated $300k+ in total revenue and helped users pay off debts or launch side businesses.
Built for Boulder Public Library, this secure AI tool turns meeting transcripts into concise summaries and enables real-time Q&A with notes. I treated it like a consultative engagement: discovery with leadership, proof-of-concepts, demos, and objection handling around privacy. Adoption spread to 200+ staff.
What started as a side hustle flipping items became a platform teaching thousands how to generate $1,000–$5,000/month part-time. Alongside a full course and playbooks, I built tools like FlippAI to scale flipping into a SaaS-powered system. Altogether, the venture generated $300k+ while sharpening my skills in consultative selling, demos, and user training.
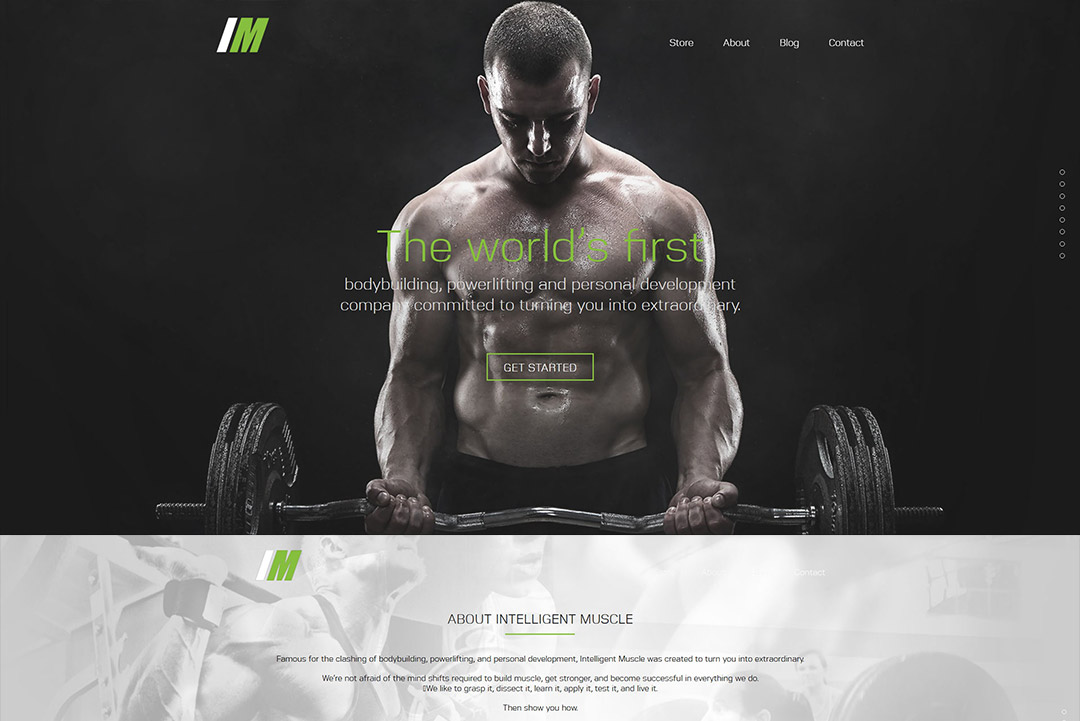
In my early 20s, I built and launched IntelligentMuscle.net—an automated digital fitness program for men looking to gain muscle mass. Through targeted Facebook ads, it generated $8k in just three weeks. Beyond the tech stack (website, backend, payment/delivery systems), I learned how to retain 80% of refund-seeking customers by hopping on calls, asking questions, and reframing value—an early training ground in consultative selling.
As a marketing consultant for real estate investors, I authored The One Page Marketing Plan for Real Estate Investors to generate leads and position myself as a trusted advisor. From there, I designed USP-driven websites and direct mail campaigns, ran discovery calls, and closed $1,000/month retainers. One client landed just three leads through my system—and turned them into $150k+ in profits.
My personal cyber lab and sales-engineering sandbox — where I turn technical projects into clear, business-focused stories. Part lab, part portfolio, part personal demo environment.